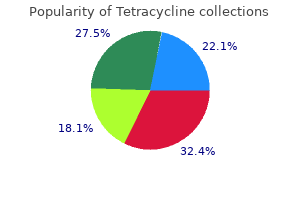
"Purchase discount tetracycline, antimicrobial fabric".
M. Marius, M.B. B.CH. B.A.O., M.B.B.Ch., Ph.D.
Clinical Director, East Tennessee State University James H. Quillen College of Medicine
They may try to follow these standards so that other people will see them as good. Children in the conventional level might say that Heinz should steal the drug because then he could save his wife and people would think of him as a hero. Postconventional the last level Kohlberg describes is what we usually mean by moral reasoning. A person evaluating a moral choice using postconventional reasoning examines the rights and values involved in the choice. Kohlberg described how self-defined ethical principles, such as a personal conviction to uphold justice, might be involved in the reasoning in this stage. Those doing the reasoning might weigh the merit of altruism or limiting certain rights for the good of the group. For the first time, the morality of societal rules are examined rather than blindly accepted. One researcher, Carol Gilligan, pointed out that Kohlberg developed the model based on the responses of boys. When girls were later tested, she continued, Kohlberg placed their responses into lower categories. Perhaps some gender-based developmental difference occurs in how we develop our morals and ethics. Boys might have moral rules that apply in every context, while girls might want to know more about the situation and relationships of the people involved before making a moral decision. Specifically, researchers are interested in how we develop our ideas about what it means to be male and female and in developmental differences between genders. Different cultures encourage different gender roles, which are behaviors that a culture associates with a gender. A behavior considered feminine in one culture, such as holding hands with a friend, might be considered masculine or not gender specific in another. Different psychological perspectives provide different theories that try to explain how gender roles develop. Biopsychological (neuropsychological) theory Biopsychogical psychologists concentrate on the nature element in the nature/nurture combination that produces our gender role. For the purposes of this book, going into extensive detail about all the differences between male and female brains is unnecessary. One of the most significant findings is that, on average, women have larger corpus callosums (see. Theoretically, this difference may affect how the right and left hemispheres communicate and coordinate tasks. However, his views about gender role development are widely known (and sometimes referred to in the media) and so are worth mentioning. Proper gender development occurs when a child realizes that she or he cannot hope to beat their same-sex parent at this competition and identifies with that person instead, girls learning to be a woman like mom or boys being a man like dad. Social-Cognitive theory Social and cognitive psychologists concentrate on the effects society and our own thoughts about gender have on role development. For example, boys are more often encouraged in rough physical play than are girls. Cognitive psychologists focus on the internal interpretations we make about the gender message we get from our environment. Gender-schema theory explains that we internalize messages about gender into cognitive rules about how each gender should behave. If a girl sees that her little brother is encouraged to wrestle with their father, she creates a rule governing how boys and girls should play. You read in your philosophy class textbook that humans are born "tabula rasa" or "blank slates. Humans may be born without reflexes and instincts, but we are born with the ability to learn them. Humans are born without instincts or other mechanisms in place to help us survive. Humans are born with a certain number of neurons, but most develop later as we learn. Most prenatal influences on humans are genetic or hormonal in origin except for (A) teratogens.
The next section of this Chapter continues to examine, in detail, the nature of investigative power provisions, both as found in multilateral instruments and as reported at the national level through the Study questionnaire. It does so for the powers of: (i) search and seizure; (ii) preservation of computer data; 35 36 37 38 Comprehensive investigative powers for Ibid. Six of these to in paragraph (a) or (e) and any other programme or data held in the instruments also provide computers. Less than 20 per cent of responding countries indicated the existence of cyber-specific powers for search or seizure. Just under 10 per cent of countries reported that there was no power at all for search and seizure at least for computer data. One country from Western Asia, for example, stated that `In relation to accessing equipment and hardware, the Criminal Procedure Code deals with the case of physical access by members of the judicial police to homes, but does not address electronic crime. These texts do not allow members of the judicial police to enter electronic networks and email on the grounds of suspicion of commission of an offence. As a result, computer data is typically stored only for the amount of time for which it is needed for processing. In addition to the pragmatic cost implications of data storage, many countries also have data protection frameworks that specify that data must not be retained for periods longer than that required by Expedited preservation of data: National the purposes for which the data are processed. For the purposes of subsection (1), data includes traffic data and subscriber information. An order made under subsection (1) shall remain in force until such time as may reasonably be required for the investigation of an offence; where prosecution is instituted, until the final determination of the case; or until such time as the Judge in Chambers deems fit. In this respect, however, it should be noted that international human rights mechanisms have held that mere storage of information about an individual amounts to an interference with rights to private life. Nonetheless, preservation of data represents an important measure for maintaining vital evidence prior to a full order for disclosure in particular in the context of transnational investigations. Nonetheless, country responses also indicated that general provisions could cover the measure in various ways. Another 29% 22% country in Southern Africa also Cyberspecific powers explained that computer data can be General powers preserved according to its legislation 6% Both by means of computer seizure, and one country in Western Europe Neither noted that it uses general provisions 41% on seizure of correspondence and Source: Study cybercrime questionnaire. The absence of legal authority for such a fundamental investigative tool presents a significant challenge not only for those particular countries, but also for any other country wishing to seek investigative assistance. Orders for computer data As discussed in Chapter One (Connectivity and cybercrime), a large part of the infrastructure and computer systems used for internet communications are owned and operated by the private sector. Internet service providers, as well as electronic communication providers and web-service providers, therefore route, store, and control a significant amount of computer data related to internet connections, transactions, and content. The use of coercive measures, such as search and seizure, by law enforcement for obtaining these data are unfeasible in the majority of circumstances due both to the volume of individual cases investigated, and disruption to legitimate business activity. Orders to such third parties to the investigation for computer data thus provide a due legal process route to obtaining electronic evidence. Order for computer data: National example from a country in the Americas If a magistrate is satisfied on the basis of an application by a police officer that specified computer data, or a printout or other information, is reasonably required for the purpose of a criminal investigation or criminal proceedings, the magistrate may order that(a) a person in the territory of <country> in control of a computer produce from the computer specified data or a printout or other intelligible output of that data; (b) an Internet service provider in <country> produce information about persons who subscribe to or otherwise use the service; or (c) a person in the territory of <country> who has access to a specified computer process and compile specified computer data from the computer and give it to a specified person Accordingly, five international or regional cybercrime instruments contain specific provisions regarding orders for obtaining stored data. The order only applies therefore, to the extent that the data are in existence at the time of the order, and can be retrieved by the subject of the order. The existence of such investigative powers alone does not in itself oblige service providers to collect or retain information they would not otherwise so process. This can be important where multiple service providers are involved in processing computer data or electronic communications. In addition to the influence of Cyberspecific powers international and regional Subscriber data (n=49) General powers cybercrime instruments, this Both may also reflect a common Neither need for this type of data, Content data (n=50) and a requirement on behalf of service providers for clear legal powers and 0% 20% 40% 60% 80% 100% procedures in requesting Source: Study cybercrime questionnaire. This is supported by comments from Order for traffic data: National example from responding countries. One country in the Americas, a country in Oceania for example, stated that, although providers often Disclosure of traffic data cooperate with law enforcement agencies voluntarily, Where a magistrate is satisfied on the basis of an application by any police officer that specified the application of existing general procedural data stored in a computer system is reasonably provisions to orders for supply of data was too required for the purpose of a criminal onerous and impractical. The country had therefore investigation or criminal proceedings, the magistrate may order that a person in control of initiated the process of adopting a cyber-specific the computer system disclose sufficient traffic provision for subscriber data orders. One country in South-Eastern was transmitted Asia, for instance, highlighted the possibility of extension of a general investigative power to order `any document or other thing. Later sections of this Chapter examine the use of powers in practice, as well as challenges faced by, and good practice used by, law enforcement in obtaining data from service providers. Real-time collection of data Orders for data represent an investigative measure for obtaining stored computer data. Crucial electronic evidence may also, however, never be stored at all (existing only in transient communications), or Figure 5.
Although the exact percentage is lacking, a significant number of children with disruptive behavior disorders have learning problems, especially in the area of verbal skills. Difficulties in reading and language may contribute to academic difficulties, especially in more advanced grades when so much depends on understanding and using the written word. Language deficits may also contribute to an inability to articulate feelings and attitudes, resulting in a child resorting to physical expression in lieu of verbal expression. Additionally, unrecognized and untreated learning disabilities and cognitive deficits create deep frustration for a child, which can lead to school avoidance/truancy. Clinicians should develop individualized treatment plans based on the specifics surrounding each case. Because of comorbidity and multiple dysfunctions, effective treatment is often multitarget, multimodal, and extensive, combining individual therapy, family therapy, pharmacotherapy, and ecological interventions (like placement and interventions designed for the school setting). Parent management training techniques are the most empirically supported programs for school-age youth. The principles underlying these approaches are: 1) reduce positive reinforcement of disruptive behavior; 2) increase reinforcement of prosocial and compliant behavior; 3) apply consequences and/or punishment for disruptive behavior, where punishment typically takes the form of time out, loss of tokens, and/or loss of privileges; and 4) make the response of parents predictable, contingent, and immediate. Pharmacotherapy may be helpful as an adjunct to treatment, for symptomatic treatment, or to treat comorbid disorders. When considering a medication trial, ensure that strong treatment alliances have been established first. Depending on the severity, persistence, or unusualness of the disruptive behavior, intensive and prolonged treatment may be necessary. These are cases in which youth have failed to demonstrate progress under the current treatment regimen. Hence, increased levels of care such as day treatment, residential, or hospitalization may be warranted, with an emphasis on the least restrictive setting for the shortest possible interval. Risks and benefits of placement in structured settings should be weighed carefully because gains typically do not continue when the youth returns to family and the community. Certain kinds of interventions will not work, for example, one-time, time-limited, short-term interventions or inoculation approaches. Such approaches are ineffective at best, and sometimes become injurious for the youth. Shock strategies, in particular, tend to result in heightened fear and/or aggression. As the field of mental health assessment and treatment advances, individual characteristics and histories will likely play an increasing role in diagnoses and in the selection of treatment modalities. Illustratively, a child from an impoverished or war-torn area who may have needed to engage in antisocial practices for survival. Regarding treatment, gender specific interventions will likely continue to experience growth, and mental health practitioners are strongly encouraged to stay abreast of developments. Garland and colleagues (2008) identified 21 common core elements that contribute to the success of evidence-based parent training and individual youth skills training treatments for children with disruptive behavior problems. In terms of therapeutic content, effective behavior problem treatments incorporate teaching behavioral principles of positive reinforcement and punishment, building the parent-child relationship, using problem-solving skills, developing anger management skills, and providing affect education. Likewise, effective techniques used by therapists when working with children with disruptive behavior problems and their caregivers include implementing behavioral principals, teaching through didactic instruction, assigning and reviewing homework, roleplaying or engaging in behavioral rehearsal, modeling, providing psychoeducational materials, and reviewing goals and progress. For mild to moderate disruptive behaviors, often the therapy is behavioral and may be implemented through parent training to address coercive parent-child interaction patterns. Recent research also confirms the effectiveness of parent training conducted in a group setting, compared to family therapy involving the parent and the child (MentalHealth. Cognitive-behavioral therapy is typically the individual psychotherapy that is used to help the children/adolescents decrease their negativity and oppositional behaviors, while improving their social-information processing skills (Behavior Guide Staff, 2006). For more significant conduct problems, a multidisciplinary and multimodal approach to treatment is highly recommended. Overall, the greater the number of risk factors and earlier they appear, the higher the risk for serious conduct problems (Offord & Kraemer, 2000). In general, treatment is not brief since establishing new attitudes and behavior patterns takes time. The research must also clearly specify the client sample and the treatment protocol using a manual. A treatment with a good level of support must have at least one study as outlined above, or two studies showing the treatment as superior to a waitlist control group.
Syndromes
- Thinking and judgment (cognitive skills)
- Help relieve cancer pain when the cancer has spread to the bones
- Kidney biopsy to confirm the diagnosis
- Candles
- Inhaled steroids to reduce lung inflammation
- Short periods without breathing
- Appetite loss
- Weight loss
- Side effect of a drug such as Dilantin or phenobarbital
- Scarring
Non-sexual probation, parole, and conditional release violations, and charges and convictions such as property offences or drug offences are not counted as sex offences, even when they occur at the same time as sex offences, or during community supervision for a sex offence conviction. Do not count offences such as failure to register as a sex offender, being in the presence of minors, or violations of alcohol or drug abstinence conditions. Definition of "Truly Imminent" For an offence to be truly imminent, it should be established based on Clear and Convincing Evidence (see page 19 for definition of thresholds of proof) that a sex offence would have occurred as part of the same behavioural sequence (minutes to hours) but for the detection and intervention from others. Examples of this nature would include an individual with a history of child molesting being discovered alone with a child and about to engage in a "naked wrestling game. Here, the intent was clearly to rape a woman, but he was interrupted by security officials. A sex offender being in the presence of children, even against his conditions of community release, is not considered "truly imminent" as the offender may choose not to molest for an indefinite period of time or even at all. Being in the presence of minor would only qualify as "truly imminent" if there was other convincing evidence, such as stated intentions to offend, or material preparations. Institutional Rule Violations Institutional rule violations resulting in institutional punishment can be counted as sex offences if certain conditions exist. The first condition is that the sexual behaviour would have to be sufficiently intrusive that a charge for a sex offence would be possible were the offender not already under legal sanction. Poorly timed or insensitive homosexual advances, consenting sexual interactions with another offender, or consenting sexual interactions with a visitor would not count even though this type of behaviour might attract institutional sanctions. The exception would be if the sexual behaviour was so flagrant that it seemed clear the offender wanted someone to witness the sexual interaction (see the discussion of targeted versus non-targeted activity below). The second condition is that the evaluator must be sure that the sexual misbehaviour actually occurred (based on a Clear and Convincing Evidence threshold see page 19), and the third condition is that it is clear the institutional punishment was in response to the sexual misbehaviour (based on the Clear and Convincing Evidence threshold - see page 19). Finally, if the punishment is an institutional move, it must also be clear that the move is to a more secure environment and not a parallel move. In a prison environment it is important to distinguish between targeted activity and non-targeted activity. Institutional disciplinary reports (with sanctions) that result from an offender who specifically chooses a female officer and masturbates in front of her, where she is the obvious and intended target of the act, would count as a "charge" and hence, could stand as an Index offence. The alternative situation is where an offender who is masturbating in his cell is discovered by a female officer and she is not an obvious and intended target. Violations of this "nontargeted" nature do not count as a "charge" and could not stand as an index offence. If the evaluator has insufficient information to distinguish between these two types of occurrences the offender gets the benefit of the doubt and the evaluator would not score these occurrences. A further important distinction is whether the masturbation takes place covered or uncovered. Masturbating under a sheet would not be regarded as an attempt at indecent exposure. Consider these two examples: 27 (1) A prisoner is masturbating under a sheet at a time when staff would not normally look in his cell. Unexpectedly a female member of staff opens the observation window, looks through the door, and observes him masturbating. This would not count as a sex offence for the purposes of Static-99R, even if a disciplinary charge and institutional punishment resulted. Prison staff have reason to believe that he listens for the lighter footsteps of a female guard approaching his cell. He times himself so that he is exposed in this fashion at the point that a female guard is looking into the cell. This would count as a sex offence for the purposes of scoring Static-99R if it resulted in an institutional punishment. An example of a behaviour that might get an inmate a disciplinary charge, but would not be used as a charge for scoring Static-99R, includes the inmate who writes an unwanted love letter to a female staff. The letter does not contain sexual content to the extent that the offender could be charged. Rule: Prison misconducts and institutional rule violations for sexual misbehaviours count as one charge per sentence Prison misconducts for sexual misbehaviours count as one charge per sentence, even if there are multiple incidents and sanctions. The reason for this is that in some jurisdictions the threshold for misconducts is very low. Often, as previously described, misconduct will involve a female guard simply looking into a cell and observing an inmate masturbating.