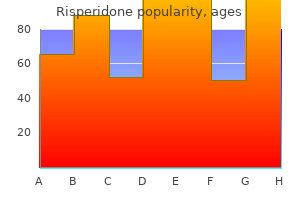
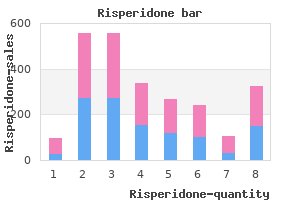
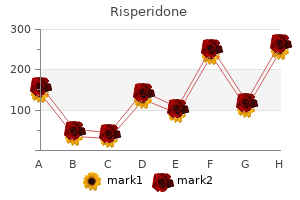
"Best 2mg risperidone, medicine 54 543".
Q. Lisk, M.A.S., M.D.
Clinical Director, Roseman University of Health Sciences
Since the rudder shaft, for example, is usually located near the quarter-chord point of the foil and since backing speeds of a ship can be a significant percentagesof the maximum forward speed, it is possible that the worst case torsional loading of the rudder shaft may be in the astern condition. The best evidence of this isthe fact that the limiting astern speed on many ships is determined during sea trials and corresponds to the speed at which the steering machinery loses control of the rudder. Cavitation occurs when the pressure at a point in the flow field drops below the vapor pressure of the fluid. At this point the fluid element "flashes" into vapor until the pressure increases to a value greater than the vapor pressure. The condition for cavitation can then be stated by the expression the vapor pressure for seawater is given in Table 15. The occurrence of cavitation can be estimated, however, by measuring surface pressure disttibution with pressure taps or pressure-sensitive paint and then using the resulting data for calculating pressure coefficients. The pressure coefficient data can then be used to calculate the local pressure (in psi) at a point on the actual control surface from the definition of pressure coefficient and from basic hydrostatic relations as where p, is the atmospheric pressure and h is the water depth at the point in question. The dynamic pressure used in this calculation should be the equivalent speed used to nondimensionalize the data. For example, suppose the control surface is tested in a simulated boundary layer in the wind tunnel and the air speed at the outboard tip of the control surface is used to nondimensionalize the wind tunnel pressure measurements. Wind tunnels have also been used to explore the performance of control surfaces as mounted on the hull of the ship. I4For these simulations a model of the underwater portion of the ship is prepared and mounted on the floor of the wind tunnel. The control surface(s) and other necessary appendages, such as propeller shafting and shafting support structure, are mounted on the hull. The control surface can be mounted with its own strain gauge balance to determine fin forces. Interference effects can also be studied by tracking the trajectory of the tip vortices with neutrally buoyant soap bubbles or smoke. Since these tests are performed on models of the entire ship, the full-scale Reynolds number can be duplicated only rarely. Since much of the control surface span is likely to be operating in the hull bonndary layer, it is likely that boundary layer control on the model hull will be needed in order to duplicate the expected boundary layer on the full-scale ship. The boundary layer thickness can be estimated by first using a potential flow analysis to obtain surface streamlines and then using a two-dimensional boundary layer method from a standard reference, for example, Young,15 to compute predicted boundary layer development. If the interference tests concern the propeller, then the propeller needs to be modeled as well. The key result was that the advance coefficient is the most important similarity parameter to match for propellers when performing wind tunnel experiments. Acoustic Sources Measurement of the strength of underwater acoustic sources is another marine topic that can be studied in the wind tunnel. Aboard most ships underwater noise is generated by four mechanisms: machinery vibration conveyed to the hull structure, flow of water past the hull, propeller operation in an unsteady flow environment, and cavitation. Much of the work on evaluation of acoustic sources on surface ships is classified and has been performed in purpose built facilities at government laboratories. The goal was to study the noise generated by a propeller on the back of a frigate, particularly the higher blade rate harmonics. The hull was fitted with antiroll fins, bilge keels, shafts, struts, propellers, and the rudder. Propeller noise is critically dependent on the flow field in which the propeller operates. Nonuniformities in this flow field can cause local cavitation and pressure pulses, that can in turn create noise. As a consequence, correctly simulating the flow field in the vicinity of the propeller disc was a high priority. Since the fullscale Reynolds number could not be achieved, suction boundary layer control was introduced upstream of the propeller blades to control the boundary layer thickness.
In addition to terror fiction, the chapbook exaggerated events from history, as with the French atrocities against the Turks in the anonymous the Life and Exploits of Napoleon Bonaparte (ca. Often drawn from newspaper accounts of bigamy, drugs and poison, disguises, romantic triangles and infidelity, divorce, misdirected or purloined letters, scandal, theft, and crime sprees, the minutiae of sensationalism suited female writers- notably, the English novelist Caroline MeyseyWigley Clive, a handicapped late-in-life wife of a Warwickshire parson. The plot of a cleverly concealed crime exonerates a wifemurderer, who thrust a small instrument into her skull, and describes the complications of his escape to Boston. In both examples, the authors stressed action and engrossing incidents above the development of character or logic. At the crest of the wave rode Braddon, the author who continued to shape the genre and reap its rewards. She parried charges that her texts armed nascent murderers with the mechanics of macabre assassinations and poisonings, the method of dispatch in the Black Band; or, the Mysteries of Midnight (1861). In response to the sweeping popularity of sensationalism in the early 1860s, an unnamed critic for the Edinburgh Review commented that the term is "the regular commercial name for a particular product of industry for which there is just now a brisk demand" (Carnell, 142). In 1866, a critic writing for Saturday Review referred to the sensational novel as "crime and crinoline" and declared it "enough to take away the breath of any quiet middle-aged gentleman" (ibid. A typically pious tsk-tsk in the Christian Remembrancer noted that these topics were elements of the times and proof that Victorians were shrugging off the restraint of principle in search of a new social ethos. Because of her dedication to the novel of sensation, Braddon was irrevocably linked to controversial elements and scandalous revelations. Against the neoclassic tide flowing toward stoicism, logic, and reason, the encouragement of sensibility in novels and drama indicated a reaction to dehumanization in literature through the elevation of intellect and wit over instinctive emotion. The sermonette is obviously the concealed voice of Radcliffe, who sets up a model of unbridled emotion in the tragedy of Signorina Laurentini/Sister Agnes, a victim of her own passions, which become sources of vice. Late 19th-century fiction began to redirect sensibility from positive emotions to a complex mix influenced by realism. In the brief story, a woman awaits widowhood as her moribund husband slips gradually from life. The sound of the personified Death approaching up the stairs and rapping on the door halt her ministrations and catapult her into lethal terror, producing two corpses as the couple lie together in death. Magazine publishing was a highly competitive business in the British Isles, Europe, and North America. Dickens fleshed out the plot with seamy details gained 314 shape-shifting from his observations while working as a crime reporter. However, the method required strictly outlining the plot and lessened opportunities for him to strengthen or refine the text or remove errors. She issued the Circular Staircase (1908) in All-Story Magazine from November 1907 to March 1908 and negotiated with the Saturday Evening Post to serialize the Wall (1938) for $65,000. By depicting Satan as a shape-shifter who roamed at large in an infinite number of forms, clerics terrified gullible parishioners into fighting any destabilizing element in their midst. In the Re- Shelley, Mary 315 naissance, the reviled image of an agile shapealtering demon arose from powerful propaganda, Malleus Maleficarum (The hammer of evildoers, 1486), the chief text of anti-Satanists. Journalist Richard Marsh set a flexible insect in Egypt for the Beetle (1897), a Victorian thriller about a vengeful female that the author describes as "a creature born neither of God nor man" (Marsh, 364). As a cultural icon, the text spawned its own subgenre of horror fiction, drama-and, later-films and computer games. Pancras Church to read and write over her remains in the hopes of pleasing the spirit of the famous feminist. The couple lived in France until the suicide of his wife, Harriet Westbrook Shelley. Thus, in a modernized form of portable horror, human dread grips his victims wherever he roams. She also expressed some of her disappointment in marriage to a man who preferred to talk with male friends to the exclusion of his wife. Mary Shelley completed Valperga (1823) and the Last Man (1826), her most successful novel, a fanciful account of an epidemic that wipes out humanity. Shelley, Percy Bysshe (17921822) Amid a confederacy of romantic poets and writers, Percy Bysshe Shelley developed a unique strand of Gothicism. Shelley regularly borrowed romances at short Gothic fiction 317 the Brentford circulating library.
Good perimeter defenses and limited on-base rapid-reaction forces are generally adequate to defeat such threats, although the 2012 Camp Bastion attack is a reminder that, if there are lapses in defenses, even less capable adversaries can exploit them. Effects of Ground Attacks on Air Bases A single ground attack on an airfield, if well planned and executed, might destroy a large number of aircraft, cause significant personnel losses, and damage or destroy a few critical assets. Such an attack might be consequential, particularly in smaller conflicts, in which the political impact of a successful attack could turn public opinion against the operation. Moreover, attacks on air bases would have to be sustained over days and weeks across many airfields. This is difficult to do with missiles and aircraft, let alone light ground forces. The probability that small ground forces alone could create this level of damage and sustain it over time at many locations is low. This is not an excuse for complacency but does suggest that such attacks would likely play a supporting, rather than primary, role in adversary-nation strategies to counter U. Christensen and colleagues at Harvard Business School developed the concept of disruptive innovation to describe how market-dominant companies can lose market share or even be driven out of business by technological or business-model innovations that, at first blush, seem uncompetitive. First, and somewhat surprising, the market-dominant company is often quite knowledgeable about the emerging technology. This is because the emerging technology underperformed on the metrics that mattered most to the company and its clients. For example, Christensen describes the case of the 8-inch computer hard drive displacing the 14-inch hard drive, which, until the mid-1980s, was the standard in mainframe computers. The metrics that mattered to management and customers were cost per megabyte of storage, access time, and total capacity. The existing 14-inch drive won on all three: It was cheaper per megabyte and much faster and had roughly ten times the total storage capacity. The 8-inch drive could offer only smaller volume, lighter weight, and lower total cost. The addition of a quality hard drive spurred demand for minicomputers, which, in turn, created a great demand for 8-inch drives. Within a few years, 8-inch drive performance had improved so much that it displaced the 14-inch drive in mainframes. This was only the first in a series of disruptive changes in computer hard-disk technology-most notably, the 5. Chinese missiles have also become far more accurate and are now better suited to strike regional air bases, logistics facilities, and other ground-based infrastructure, which Chinese military analysts have concluded are 107 vulnerabilities in modern warfare. Stokes and Ian Easton, Evolving Aerospace Trends in the AsiaPacific Region: Implications for Stability in the Taiwan Strait and Beyond, Arlington, Va. When tied to advanced sensors and a robust command and control system, mobile ballistic missiles offer some of the benefits of a first-class air force to nations whose air forces are weak or developing. Although ballistic missiles are more costly than aircraft to deliver larger numbers of weapons during a prolonged conflict, they could be decisive in a short war under some conditions. Specifically, ballistic-missile attacks on air bases and aircraft carriers have the potential to destroy many aircraft and heavily damage runways and aircraft carriers,111 disrupting sortie generation so severely that an adversary might achieve its military 108 109 Which is not to say that the United States currently possesses a robust defense against aircraft and cruise missiles, just that it is a more manageable problem than ballistic-missile defense. The problem of intercepting ballistic missiles is complex and well beyond the scope of this report. For our purposes, the essence of the problem is that the United States has yet to deploy a theater missile defense system that can defeat large attacks and is unlikely to in the near future. The DoD 2010 review of ballistic-missile defense programs admits this, noting that "these capabilities exist in numbers that are only modest in view of the expanding regional missile threat. For an overview of the missile defense problem, see National Research Council, Making Sense of Ballistic Missile Defense: An Assessment of Concepts and Systems for U. We are not suggesting that China will replace the United States as the market-dominant power projector, as can happen in business disruptive innovations but rather that Chinese innovations could overturn the U. Chinese Analysts Consider the Antiship Ballistic Missile," Naval War College Review, Vol. Work, Range, 111 110 34 and political objectives before the United States could effectively intervene.
Let z(P) be the total demand of vertices in set P and a(P) be the total supply of vertices in P. How would we construct a static flow model to simulate this dynamic flow problem so that a maximum static flow in the new network would correspond to a maximum dynamic flow? Suppose an undirected flow network is a planar graph and a (at the left side) and z (at the right side) are both on the unbounded region surrounding the network. Draw edges extending infinitely to the left from a and to the right from z; give them infinite capacity. This divides the unbounded region into two unbounded regions, an upper and a lower unbounded region. Thus, a shortest such path in the dual network is a minimum az cut in the original network. Suppose an undirected flow network N is a planar graph and a (at the left side) and z (at the right side) are both on the unbounded region surrounding the network. Starting from a, build an az flow path by choosing at each vertex x the first unsaturated edge in clockwise order starting from the edge used to enter x. Prove that repeated use of the augmenting flow algorithm yields a maximum flow in a finite number of applications for networks with irrational capacities provided that vertices are ordered (indexed) and that the next vertex scanned in Step 2 of the algorithm is the labeled vertex with lowest index. Write a program to find maximum flows in directed networks (the networks are input data). Write a program to find the maximum number of paths in an undirected graph between two given vertices such that the following are true: (a) the paths are edge disjoint. Write a program that when given a network with an az flow of value k, will extract from the flow k unit-flow paths from a to z. Write a program to find, for a given pair of vertices a and b in a given connected graph, a minimum set of vertices whose removal disconnects a from b (see Exercise 29). Recall that a bipartite graph G = (X, Y, E) is an undirected graph with two specified vertex sets X and Y and with all edges of the form (x, y), x X, y Y. We let X and Y be the two sets to be matched and edges (x, y) represent pairs of elements that may be matched together. A matching in a bipartite graph is a set of independent edges (with no common endpoints). As with network flows, we cannot always obtain a maximum matching in a bipartite graph by simply adding more edges to a non-maximum matching. A typical matching problem involves pairing off compatible boys and girls at a dance or the one-to-one assignment of workers to jobs for which they are trained. In the bipartite graph model, we make one X-vertex for each subset, one Y-vertex for each element, and an edge (x, y) whenever element y is in subset x. Conversely, any matching problem can be modeled as a set-of-distinct-representatives problem. The capacities of the edges from X to Y can be any large positive integers, but it is convenient to assume that these capacities are. Although this matching cannot be extended, we still wonder whether a complete X-matching is possible. As has happened before in flow problems, we have made a "mistake" in this matching and now need to make some reassignments. We convert this matching into the corresponding flow in the associated matching network: darkened edges in Figure 4. From a, the only outgoing edge that is not saturated is (a, c), since c is the only X-vertex not involved in the initial matching. From c we can label the two Y-vertices, g and i, adjacent to c with the label (c+, 1). Then there must be an incoming edge to g with positive flow, namely (b, g), coming from the unlabeled X-vertex b. We have possible matches of c with g and i, but to make either match, we must sever the current match of g with b or of i with f and rematch b or f with other Y-vertices-in this network, b can be rematched with j or f rematched with m. Now either d can be matched with h (currently unmatched) or e can be matched with k (also currently unmatched). The fact that h and k are unmatched is reflected in the fact that from either h or k one can label z. If we label z (k+, 1), the augmenting flow chain prescribed by the algorithm is acgbjekz. Our augmenting flow chain specifies that we add edge (c, g) to our matching, remove edge (b, g), add edge (b, j), remove edge (e, j), and add edge (e, k).